New Orleans hit with a cyberattack, 4K computers affected
The city of New Orleans was the latest major U.S. city hit by a cyberattack this past Friday, December 13, 2019. It follows attacks on Atlanta in 2018 and Baltimore earlier this year. The malware was discovered in the morning. The IT staff ordered all computers to power off to avoid the malware from spreading. The outage caused the city to declare a state of emergency. Luckily no data was held for ransom, but the recovery process will be costly and lengthy.
No request for ransom has been received thanks to the attack being stopped in the early stages.
"But there were still headaches and disruptions as city employees arrived at work Monday, and New Orleans police were forced to use paper and pens to conduct basic tasks like writing arrest reports."
According to NOLA.com:
"Mayor LaToya Cantrell said about 4,000 computers will need to be scrubbed. She added that 400 servers were affected. The exact nature and extent of the attack were unclear, but it appears to have started about 5 a.m. Friday, when city officials first noticed suspicious activity on their network. Reports of suspicious activity picked up as employees got to work around 8 a.m., and officials decided to shut down the system after 11 a.m."
The police department, 911 and 311 were unaffected, and the fire department is operating off old-fashioned hard copies. Sounds like NOLA had functioning backups, unlike many other cities that have recently fallen victim to ransomware.
To read more follow the link to Nola.com
https://www.nola.com/news/politics/article_0a132564-2061-11ea-8d52-53848745f381.html
VISA warns of POS malware incidents at gas pumps across North America
VISA says it's aware of POS malware being deployed on the networks of five North American fuel dispenser merchants.
The payments processor said that gas station operators are under attack by cybercrime groups who want to deploy point of sale malware on fuel dispenser networks.
"POS malware works by continuously scraping a computer's RAM for what looks like unencrypted payment card data, which it collects, and then uploads to a remote server.
The VISA Payment Fraud Disruption (PFD) team says cybercrime groups appear to have found a weak spot in how gas stations and gas pump operators work."
The problem basically is out of date readers that do not accept cards with chips but rely on the magnetic strip. When a card is swiped the data is sent unencrypted and that is when the crooks intercept the data.
"VISA said the easiest ways for fuel dispenser merchants to safeguard customers is to either encrypt card data while it's being transferred across a network or stored in memory or shift to a chip card acceptance policy."
The entire article can be found at the following link;
https://www.zdnet.com/article/visa-warns-of-pos-malware-incidents-at-gas-pumps-across-north-america/?ftag=TRE-03-10aaa6b&bhid=27630927001468733386426006914379
Take your cybersecurity seriously. Make sure your computer OS and anti-virus are up to date. Apply firmware patches to your routers and beware when opening emails, even if it purports to be from someone you know. A lot of phishing attacks use spoofing to gain the confidence of the target.
Support for Windows 7 ends 01/14/2020.
After January 14, 2020, Microsoft will no longer provide security updates or support for PCs with Windows 7. Upgrade to Windows 10 now to keep your employees productive and secure.
https://support.microsoft.com/en-us/help/4057281/windows-7-support-will-end-on-january-14-2020
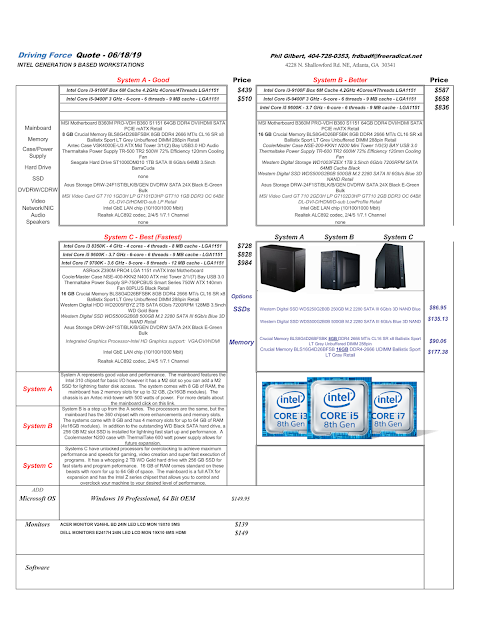
DForce Intel Gen 8 & 9 Workstations
Tuesday, December 17, 2019
Thursday, December 12, 2019
How to be Safe Shopping Online during the Holiday Season. Top 3 Phishing attempts of 2019.
FBI shares security advice for online shopping
FBI: Use credit cards rather than debit cards, don't use public WiFi, keep your devices updated, and more.
The FBI has issued a list of 12 things you should do during the holiday shopping season. If you do fall victim to a holiday scam the FBI wants you to report the crime to it's Internet Crime page
By reporting the crime you help the FBI to understand trends and help it in fighting these activities.
Read all the tips at the following link;
https://www.zdnet.com/article/fbi-shares-security-advice-for-online-shopping/?ftag=TRE-03-10aaa6b&bhid=2219791
Microsoft details the most clever phishing techniques it saw in 2019
This year's most clever phishing tricks include hijacking Google search results and abusing 404 error pages.
In the year 2019, Microsoft said that out of the total volume of emails analyzed by the company, phishing emails grew as a percentage from .2% in January of 2018 to .6% by October of 2019.
There were 3 attacks identified by Microsoft as being most clever;
1. Hijacking search results
The first is a multi-layered malware operation through which a criminal gang poisoned Google search results.
2. Abusing 404 error pagesWhen a 404 page is displayed it indicates that the link is broke or non-existent. Hackers are using links that takes one to a supposedly non-existent page but is hosted on phishing website. If a security system scans the link and receive a 404 error it will ignore the site, however, if a real user clicks on the link the phishing site could detect the user and redirect to a phishing page.
3. MitM-based phishing (Man in the Middle)
I've written about this attack in previous blogs. It is one that my Office 365 online users will be familiar with.
An attacker will send a phishing email, usually saying that something is wrong with your Office 365/Exchange account or that you have received an attachment, a PDF or Voicemail. Upon clicking on the link you will be presented with a familiar login screen. Web pages are easy to duplicate by capturing the underlying source code. The key to being safe from these phishing attempts is looking at the URL displayed in the address space.
To read more about these phishing attacks click on the following link;
https://www.zdnet.com/article/microsoft-details-the-most-clever-phishing-techniques-it-saw-in-2019/?ftag=TRE-03-10aaa6b&bhid=2219791
Thursday, November 21, 2019
Beware of Fake Software updates... Malware Attacks on Hospital are rising fast
This fake software update tries to download malware onto your PC even when you click 'later'
According to W3Techs, WordPress powers 34% of all the websites on the Internet, including those without a content management system (CMS) or with a custom-coded CMS. Or to put it another way, WordPress powers over one-third of the web! And if you limit the data set to only websites with a known CMS, WordPress’ market share gets even more dominant. WordPress holds a 60% market share for content management systems on websites with a known CMS. (Kinsta.com)
That said crooks are hacking into insecure WordPress sites through a vulnerability in the theme plugin and interjecting malicious redirect scripts into the site. What happens when the script runs is an alert will pop up with a fake Flash update message. The user can click on Update Now or Later, either way, the redirect still occurs and the malicious payload is delivered.
The payload is what is known as a RAT, Remote Access Trojan which allows remote access to the compromised computer.
A second known way the RAT payload is delivered is if the Chrome Browser is being used to visit a compromised website, a message that the 'PT Sans' font wasn't found and to update the browser.
Be careful and vigilant, especially with the upcoming holiday season when cyber-crooks will be active trying to cash in on consumer holiday buying.
To read more click on the following link;
https://www.zdnet.com/article/this-fake-software-update-tries-to-download-malware-onto-your-pc-even-when-you-click-later/?ftag=TRE-03-10aaa6b&bhid=2219791
Two-factor authentication. What is it and how to deploy.
The single most important security precaution you can take with high-value online accounts is to enable a mobile device as a secondary identity factor. Which authenticator app should you choose? The correct answer might involve multiple apps.
Malware attacks on hospitals are rising fast, and the problem is about to get a lot worse
The healthcare industry stores some of the most sensitive personal information there can be about people: hackers know this and are looking to exploit what they view as an easy target.
Alongside names, addresses, dates of birth and other information that hackers can use to commit fraud and other cybercrime, the nature of health data means hospitals store extremely sensitive information about patients, something which attackers could exploit.
Coming in the next blog post, the best way to protect your credentials/online identity.
Two-factor authentication. What is it and how to deploy.
The single most important security precaution you can take with high-value online accounts is to enable a mobile device as a secondary identity factor. Which authenticator app should you choose? The correct answer might involve multiple apps.
don't miss this important info.
Driving Force Intel Gen 8 and 9 Workstations
According to W3Techs, WordPress powers 34% of all the websites on the Internet, including those without a content management system (CMS) or with a custom-coded CMS. Or to put it another way, WordPress powers over one-third of the web! And if you limit the data set to only websites with a known CMS, WordPress’ market share gets even more dominant. WordPress holds a 60% market share for content management systems on websites with a known CMS. (Kinsta.com)
That said crooks are hacking into insecure WordPress sites through a vulnerability in the theme plugin and interjecting malicious redirect scripts into the site. What happens when the script runs is an alert will pop up with a fake Flash update message. The user can click on Update Now or Later, either way, the redirect still occurs and the malicious payload is delivered.
The payload is what is known as a RAT, Remote Access Trojan which allows remote access to the compromised computer.
A second known way the RAT payload is delivered is if the Chrome Browser is being used to visit a compromised website, a message that the 'PT Sans' font wasn't found and to update the browser.
Be careful and vigilant, especially with the upcoming holiday season when cyber-crooks will be active trying to cash in on consumer holiday buying.
To read more click on the following link;
https://www.zdnet.com/article/this-fake-software-update-tries-to-download-malware-onto-your-pc-even-when-you-click-later/?ftag=TRE-03-10aaa6b&bhid=2219791
Two-factor authentication. What is it and how to deploy.
The single most important security precaution you can take with high-value online accounts is to enable a mobile device as a secondary identity factor. Which authenticator app should you choose? The correct answer might involve multiple apps.
Malware attacks on hospitals are rising fast, and the problem is about to get a lot worse
The healthcare industry stores some of the most sensitive personal information there can be about people: hackers know this and are looking to exploit what they view as an easy target.
Alongside names, addresses, dates of birth and other information that hackers can use to commit fraud and other cybercrime, the nature of health data means hospitals store extremely sensitive information about patients, something which attackers could exploit.
Coming in the next blog post, the best way to protect your credentials/online identity.
Two-factor authentication. What is it and how to deploy.
The single most important security precaution you can take with high-value online accounts is to enable a mobile device as a secondary identity factor. Which authenticator app should you choose? The correct answer might involve multiple apps.
don't miss this important info.
Driving Force Intel Gen 8 and 9 Workstations
Monday, November 4, 2019
Dark Mode, What is it and how to enable it in Windows 10
Dark Mode in Windows 10
If you are like millions of computer users the constant glare of bright white backgrounds on your computer screen can take a toll on your eyes. Maybe you have heard about Dark Mode for Windows.
Dark modes aren’t just for emos or for those who like dressing in black. They are better on the eyes and use much less battery which is ideal for phone and laptop users. I find webpages shown within a dark browser easier to read too. Something to do with the contrast I guess.
If you haven't heard of it and you suffer from eye strain then you owe it to yourself to try Dark Mode. I didn't like it at first but it was because it is so different, but now I really prefer dark mode. When I switch to the default white screens my eyes feel it instantly. Dark mode provides instant relief.
To enable Dark Mode in Windows 10 you have to click on the Settings button, then choose Personalization.
Next click on Colors, select Dark for your default Windows mode as well as your default app mode.
If you are like millions of computer users the constant glare of bright white backgrounds on your computer screen can take a toll on your eyes. Maybe you have heard about Dark Mode for Windows.
Dark modes aren’t just for emos or for those who like dressing in black. They are better on the eyes and use much less battery which is ideal for phone and laptop users. I find webpages shown within a dark browser easier to read too. Something to do with the contrast I guess.
If you haven't heard of it and you suffer from eye strain then you owe it to yourself to try Dark Mode. I didn't like it at first but it was because it is so different, but now I really prefer dark mode. When I switch to the default white screens my eyes feel it instantly. Dark mode provides instant relief.
To enable Dark Mode in Windows 10 you have to click on the Settings button, then choose Personalization.
Next click on Colors, select Dark for your default Windows mode as well as your default app mode.
Upon turning on Dark Mode, the most noticeable differences will be Windows Explorer and title bars on certain applications.
To really get the full-blown effect of Dark Mode across your entire computing environment, you need to change settings in Office 2016/365 and Google Chrome.
Dark Mode in Microsoft Office
To enable Dark Mode in Microsoft Office, (BTW, this is supported in Office 2016, 365 and 2013), follow the instructions provided by the following link;
Dark Mode in Google Chrome
Firefox and Microsoft Edge were leaders in the implementation of dark mode.
Now Google's Chrome browser also has a dark mode feature. To enable dark mode in Chrome, you first have to enable it on Windows 10 as described above. Once you have enabled it on Windows 10, open Chrome and type the following in the address bar;
chrome://flags
Next search flags for Dark Mode, it is an extension that you can enable or disable within the browser.
Enable the dark mode extension.
Firefox and Microsoft Edge were leaders in the implementation of dark mode.
For a less techy approach, use the following link and read how to change Chrome to dark mode and customize the look;
DFORCE Intel Generation 8 and 9 workstations
Wednesday, October 23, 2019
Malware alerts, Ransomware and Sextortion emails, Alexa and Google Home eavesdropping
Phishing alert: This fake email about a bank payment delivers trojan malware
An old highly customizable trojan malware is being distributed via email in a new phishing campaign claiming that a payment is being made to your bank account. This trojan first appeared in 2016. It is known as the Remcos remote access trojan and has been modified since its first appearance.
Available to crooks for as little as $58, the malware is an information stealer and surveillance tool, using capabilities including keylogging, taking screenshots and stealing clipboard contents to secretly take usernames and passwords from infected victims.
The email is delivered with an attached zip file containing the malicious code. It attempt to trick you into opening the zip file which purportedly contains info about the deposit into your bank account. The zip file contains a gateway to a .TXT extension which will run a PowerShell script installing the malware onto the Windows machine. It will add itself to auto-start when the machine is powered up.
Read more at this link;
https://www.zdnet.com/article/phishing-alert-this-fake-email-about-a-bank-payment-delivers-trojan-malware/
Major German manufacturer still down a week after getting hit by ransomware
Pilz, a German company making automation tool, was infected with the BitPaymer ransomware on October 13.
https://www.zdnet.com/article/major-german-manufacturer-still-down-a-week-after-getting-hit-by-ransomware/
Ransomware: These are the most common attacks targeting you right now
An analysis of ransomware reporting over the past six months shows that while there's a big focus on big targets, going after individual users is still very popular.
Recent ransomware attacks targeting schools, hospitals, and local governments might suggest that cybercriminals have shifted away from distributing file-encrypting malware to individuals in favor of going after whole networks. But the most common ransomware campaign of the last six months is targeting home users.
The most common ransomware targeting home users, over 56% belongs to one family of malware which first appeared in 2018. Known as Stop - aka DJVU, it is almost karma since it is mainly distributed by torrent websites. These sites typically distribute cracked software and movies where individuals attempt to get the product without paying for it. The malware is often hidden in these cracked versions.
to read more about this, click the following link;
https://www.zdnet.com/article/ransomware-these-are-the-most-common-attacks-targeting-you-right-now/
Phorpiex botnet made $115,000 in five months just from mass-spamming sextortion emails
Sextortion emails look silly for most of us, but there are many users who take them at face value and pay up.
Recently there has been a rise in emails purporting to have compromising images of their targets acquired from their webcam by the placement of a trojan or malware when the targetted user visited an adult website. In all cases, the sender of the email wants to blackmail the target by threatening to send videos or pictures to the targets contact list. The payoff is to be made in bitcoin to a link within the email. These are known as "sextortion schemes".
There have been 5 waves of these schemes since April 2019. In some of the emails, the spammer will even have an old password acquired through one of the many breaches of banks, credit cards, and other valid sites. BTW, if you have received one with an old password and still employ that password, be sure to change that password on any site you still use.
This uptick in use of this attack has been attributed to a spam botnet, call Phorpiex or "Trik". The Phorpiex botnet made $115,000 in five months just from mass-spamming sextortion emails
"According to a report shared with ZDNet last week, some of these mass-mailed sextortion waves peaked at 27 million emails per campaign, with some of the Phorpiex-infected computers sending out up to 30,000 sextortion emails per hour -- when the botnet was maxing out."
This botnet is not new and researchers now say most targetted victims were part of a breach and could have found they were compromised within the "Have I Been Pawned" database. How many blogs have I written imploring readers to check to see if they were part of a breach? https://haveibeenpwned.com/
To read more, use the links below;
https://www.zdnet.com/article/phorpiex-botnet-made-115000-in-five-months-just-from-mass-spamming-sextortion-emails/?ftag=TRE-03-10aaa6b&bhid=27630927001468733386426006914379
Inside the mind of a sextortion scam artist
Do they really have access to your browsing habits and data?
https://www.zdnet.com/article/inside-the-mind-of-a-sextortionist-scam-artist/
Alexa and Google Home devices leveraged to phish and eavesdrop on users, again.
Exclusive: Amazon, Google fails to address security loopholes in Alexa and Home devices more than a year after first reports.
It should be no surprise that Smart Assistants are being utilized by hackers to eavesdrop on unsuspecting owners and trick them into handing over sensitive data.
Technically, the attacks against Amazon and Google Home smart assistants aren't new. The first attacks against the devices surfaced in April 2018. Countermeasures and patches were enacted then, however, hackers are finding new avenues to exploit the devices.
The latest was discovered by Researchers at SRLabs. Backend code that both Amazon and Google provide App developers is being used by hackers for phishing and eavesdropping.
These backends provide access to functions that developers can use to customize the commands to which a smart assistant responds, and the way the assistant replies.
The SRLabs team discovered that by adding the "�. " (U+D801, dot, space) character sequence to various locations inside the backend of a normal Alexa/Google Home app, they could induce long periods of silence during which the assistant remains active.
to read more, click on the following link;
https://www.zdnet.com/article/alexa-and-google-home-devices-leveraged-to-phish-and-eavesdrop-on-users-again/?ftag=TRE-03-10aaa6b&bhid=27630927001468733386426006914379
New DForce Intel Generation 9 based Workstations
Intel's Generation 8 and 9 based workstations represent huge improvements over prior generations. Performance gains from the increased number of cores and larger cache are two of the many enhancements you gain from a new workstation based on these CPUs. SSDs (solid-state drives) have never been so affordable and the read/write performance is dramatically noticeable.
An old highly customizable trojan malware is being distributed via email in a new phishing campaign claiming that a payment is being made to your bank account. This trojan first appeared in 2016. It is known as the Remcos remote access trojan and has been modified since its first appearance.
Available to crooks for as little as $58, the malware is an information stealer and surveillance tool, using capabilities including keylogging, taking screenshots and stealing clipboard contents to secretly take usernames and passwords from infected victims.
The email is delivered with an attached zip file containing the malicious code. It attempt to trick you into opening the zip file which purportedly contains info about the deposit into your bank account. The zip file contains a gateway to a .TXT extension which will run a PowerShell script installing the malware onto the Windows machine. It will add itself to auto-start when the machine is powered up.
Read more at this link;
https://www.zdnet.com/article/phishing-alert-this-fake-email-about-a-bank-payment-delivers-trojan-malware/
Major German manufacturer still down a week after getting hit by ransomware
Pilz, a German company making automation tool, was infected with the BitPaymer ransomware on October 13.
https://www.zdnet.com/article/major-german-manufacturer-still-down-a-week-after-getting-hit-by-ransomware/
Ransomware: These are the most common attacks targeting you right now
An analysis of ransomware reporting over the past six months shows that while there's a big focus on big targets, going after individual users is still very popular.
Recent ransomware attacks targeting schools, hospitals, and local governments might suggest that cybercriminals have shifted away from distributing file-encrypting malware to individuals in favor of going after whole networks. But the most common ransomware campaign of the last six months is targeting home users.
The most common ransomware targeting home users, over 56% belongs to one family of malware which first appeared in 2018. Known as Stop - aka DJVU, it is almost karma since it is mainly distributed by torrent websites. These sites typically distribute cracked software and movies where individuals attempt to get the product without paying for it. The malware is often hidden in these cracked versions.
to read more about this, click the following link;
https://www.zdnet.com/article/ransomware-these-are-the-most-common-attacks-targeting-you-right-now/
Phorpiex botnet made $115,000 in five months just from mass-spamming sextortion emails
Sextortion emails look silly for most of us, but there are many users who take them at face value and pay up.
Recently there has been a rise in emails purporting to have compromising images of their targets acquired from their webcam by the placement of a trojan or malware when the targetted user visited an adult website. In all cases, the sender of the email wants to blackmail the target by threatening to send videos or pictures to the targets contact list. The payoff is to be made in bitcoin to a link within the email. These are known as "sextortion schemes".
There have been 5 waves of these schemes since April 2019. In some of the emails, the spammer will even have an old password acquired through one of the many breaches of banks, credit cards, and other valid sites. BTW, if you have received one with an old password and still employ that password, be sure to change that password on any site you still use.
This uptick in use of this attack has been attributed to a spam botnet, call Phorpiex or "Trik". The Phorpiex botnet made $115,000 in five months just from mass-spamming sextortion emails
"According to a report shared with ZDNet last week, some of these mass-mailed sextortion waves peaked at 27 million emails per campaign, with some of the Phorpiex-infected computers sending out up to 30,000 sextortion emails per hour -- when the botnet was maxing out."
This botnet is not new and researchers now say most targetted victims were part of a breach and could have found they were compromised within the "Have I Been Pawned" database. How many blogs have I written imploring readers to check to see if they were part of a breach? https://haveibeenpwned.com/
To read more, use the links below;
https://www.zdnet.com/article/phorpiex-botnet-made-115000-in-five-months-just-from-mass-spamming-sextortion-emails/?ftag=TRE-03-10aaa6b&bhid=27630927001468733386426006914379
Inside the mind of a sextortion scam artist
Do they really have access to your browsing habits and data?
https://www.zdnet.com/article/inside-the-mind-of-a-sextortionist-scam-artist/
Alexa and Google Home devices leveraged to phish and eavesdrop on users, again.
Exclusive: Amazon, Google fails to address security loopholes in Alexa and Home devices more than a year after first reports.
It should be no surprise that Smart Assistants are being utilized by hackers to eavesdrop on unsuspecting owners and trick them into handing over sensitive data.
Technically, the attacks against Amazon and Google Home smart assistants aren't new. The first attacks against the devices surfaced in April 2018. Countermeasures and patches were enacted then, however, hackers are finding new avenues to exploit the devices.
The latest was discovered by Researchers at SRLabs. Backend code that both Amazon and Google provide App developers is being used by hackers for phishing and eavesdropping.
These backends provide access to functions that developers can use to customize the commands to which a smart assistant responds, and the way the assistant replies.
The SRLabs team discovered that by adding the "�. " (U+D801, dot, space) character sequence to various locations inside the backend of a normal Alexa/Google Home app, they could induce long periods of silence during which the assistant remains active.
to read more, click on the following link;
https://www.zdnet.com/article/alexa-and-google-home-devices-leveraged-to-phish-and-eavesdrop-on-users-again/?ftag=TRE-03-10aaa6b&bhid=27630927001468733386426006914379
New DForce Intel Generation 9 based Workstations
Intel's Generation 8 and 9 based workstations represent huge improvements over prior generations. Performance gains from the increased number of cores and larger cache are two of the many enhancements you gain from a new workstation based on these CPUs. SSDs (solid-state drives) have never been so affordable and the read/write performance is dramatically noticeable.
Monday, October 21, 2019
'Unpatchable' Flaw Can Jailbreak (and Hack) Older iPhones
A free tool from security researcher axi0mX exploits the 'bootrom' in iPhone 4s through X, and promises to make older iPhones permanently jailbreakable, regardless of iOS version.
https://www.pcmag.com/news/371032/unpatchable-flaw-can-jailbreak-and-hack-older-iphones
A free tool from security researcher axi0mX exploits the 'bootrom' in iPhone 4s through X, and promises to make older iPhones permanently jailbreakable, regardless of iOS version.
https://www.pcmag.com/news/371032/unpatchable-flaw-can-jailbreak-and-hack-older-iphones
Wednesday, September 25, 2019
Microsoft releases Emergency Security Update, please update ASAP
Microsoft releases out-of-band security update to fix IE zero-day Defender bug
Generally, Microsoft releases updates on the 2nd Tuesday of each month. However an emergency update was issued yesterday by Microsoft and it is urging Windows users to install these updates as soon as possible.
The updates patch 2 bugs, one an Internet Explorer zero-day bug is the most serious and has already been exploited in active attacks in the wild.
The attack requires luring an Internet Explorer user on a malicious website, which is a rather trivial task, as it can be achieved by various methods such as spam email, IM spam, search engine ads, malvertising campaigns, and others.
for more details about this and the other bug fix, click on the following link;
https://www.zdnet.com/article/microsoft-releases-out-of-band-security-update-to-fix-ie-zero-day-defender-bug/?ftag=TRE-03-10aaa6b&bhid=2219791
Generally, Microsoft releases updates on the 2nd Tuesday of each month. However an emergency update was issued yesterday by Microsoft and it is urging Windows users to install these updates as soon as possible.
The updates patch 2 bugs, one an Internet Explorer zero-day bug is the most serious and has already been exploited in active attacks in the wild.
The attack requires luring an Internet Explorer user on a malicious website, which is a rather trivial task, as it can be achieved by various methods such as spam email, IM spam, search engine ads, malvertising campaigns, and others.
for more details about this and the other bug fix, click on the following link;
https://www.zdnet.com/article/microsoft-releases-out-of-band-security-update-to-fix-ie-zero-day-defender-bug/?ftag=TRE-03-10aaa6b&bhid=2219791
Wednesday, September 11, 2019
Huge Patch Tuesday update, Security News: States brace for ransomware assaults on voter registries
Microsoft patches two zero-days in massive September 2019 Patch Tuesday
Microsoft's September 2019 Patch Tuesday comes with 80 fixes, 17 of which are for critical bugs.
Yesterday was the 2nd Tuesday of the month which means Patch Tuesday for Windows users. This patch includes fixes for two Zero-Day exploits. If a system downloads the malware and infects the host, an attacker can run malware on the system using administrator privileges thus spreading on a network and outside the organization. One of the exploits impacts the Winsock service, very bad malware.
"As usual, Microsoft didn't reveal any details of how the two bugs were being exploited in the wild, only acknowledging a security researcher from Qihoo 360 Vulcan Team with discovering the first."
This Patch Tuesday update is larger than all previous Patch Tuesday updates released this year.
To read more click on the following link;
https://www.zdnet.com/article/microsoft-patches-two-zero-days-in-massive-september-2019-patch-tuesday/?ftag=TREc64629f&bhid=2219791
States brace for ransomware assaults on voter registries
Hackers have recently shutdown municipal computer in Texas, Maryland, Florida, and New York. In each case, the affected users have their files held hostage and databases threatened to be erased unless a ransom is paid. Atlanta was the subject of a massive cyberattack that began March 2018.
"In response to this hack, Atlanta devoted $2.7 million to contractors in order to recover, but later estimated it would need $9.5 million.[12]
On November 26, 2018, the Department of Justice indicted two Iranian hackers for the attack, charging that Faramarz Shahi Savandi and Mohammad Mehdi Shah Mansouri were part of the SamSam group and created SamSam Ransomware"
https://en.wikipedia.org/wiki/2018_Atlanta_cyberattack
Today officials are concerned that the same types of malware will be used to shut down voter registration and polling stations in the upcoming 2020 elections.
Illinois plans to move its voter registration to a closed optical network that will be offline from other State computers and networks.
"A successful ransomware attack at a critical point before an election could limit access to information and has the potential to undermine public confidence in the election itself," DHS spokesman Scott McConnell said in a statement.
Full article at the following link;
https://www.cnet.com/news/states-prepare-for-ransomware-attacks-on-voter-registries/?ftag=CAD090e536&bhid=21042726186831923270015874178287
Other News of Note;
Wave goodbye to passwords: Soon you could unlock your PC just by holding up your hand
Hitachi Europe has developed Biometric technology that could allow PC users to unlock their computer via their webcam by scanning veins in their fingers.
Password management is a critical component of IT maintenance. Many users do not take password security seriously, using easily guessed weak passwords to protect critical information. Biometrics are already being used on modern smartphones and Microsoft's Hello technology that allows you to login with your face.
Entire article at;
https://www.zdnet.com/article/wave-goodbye-to-passwords-the-veins-in-your-fingers-could-soon-unlock-your-pc/?ftag=TRE0fb9d06&bhid=2219791
Apple unveils new iPhone 11 and iPhone 11 Pro
Apple has introduced 2 new iPhones as well as a new iPad. The base starter phone, iPhone 11 is even priced $50 less than it's predecessor. However,
"Apple kept the starting prices of its more advanced models, the iPhone 11 Pro and iPhone 11 Pro Max, at $1,000 and $1,100. The company unveiled the new phones at a 90-minute press event at its Silicon Valley campus."
Apple has rebranded its iPhone line to make the iPhone 11 its entry-level option while adding a “Pro” label to its more expensive models.
https://www.nytimes.com/2019/09/10/technology/iphone-11.html
https://www.cnbc.com/2019/09/10/apple-hardware-event-new-iphones-apple-watches-and-more.html?__source=facebook%7Cmain&fbclid=IwAR21xsWe9ebXPC9DSnCSmyDnEFj8cxRI74ooaKmW82JdvWzJVI64H7NNOOQ
George Soros offers rare praise for Trump and how he’s handled Huawei in the trade war
https://www.cnbc.com/2019/09/10/soros-offers-rare-praise-for-trumps-handling-of-huawei-in-trade-war.html
Microsoft's September 2019 Patch Tuesday comes with 80 fixes, 17 of which are for critical bugs.
Yesterday was the 2nd Tuesday of the month which means Patch Tuesday for Windows users. This patch includes fixes for two Zero-Day exploits. If a system downloads the malware and infects the host, an attacker can run malware on the system using administrator privileges thus spreading on a network and outside the organization. One of the exploits impacts the Winsock service, very bad malware.
"As usual, Microsoft didn't reveal any details of how the two bugs were being exploited in the wild, only acknowledging a security researcher from Qihoo 360 Vulcan Team with discovering the first."
This Patch Tuesday update is larger than all previous Patch Tuesday updates released this year.
To read more click on the following link;
https://www.zdnet.com/article/microsoft-patches-two-zero-days-in-massive-september-2019-patch-tuesday/?ftag=TREc64629f&bhid=2219791
States brace for ransomware assaults on voter registries
"In response to this hack, Atlanta devoted $2.7 million to contractors in order to recover, but later estimated it would need $9.5 million.[12]
On November 26, 2018, the Department of Justice indicted two Iranian hackers for the attack, charging that Faramarz Shahi Savandi and Mohammad Mehdi Shah Mansouri were part of the SamSam group and created SamSam Ransomware"
https://en.wikipedia.org/wiki/2018_Atlanta_cyberattack
Today officials are concerned that the same types of malware will be used to shut down voter registration and polling stations in the upcoming 2020 elections.
Illinois plans to move its voter registration to a closed optical network that will be offline from other State computers and networks.
"A successful ransomware attack at a critical point before an election could limit access to information and has the potential to undermine public confidence in the election itself," DHS spokesman Scott McConnell said in a statement.
Full article at the following link;
https://www.cnet.com/news/states-prepare-for-ransomware-attacks-on-voter-registries/?ftag=CAD090e536&bhid=21042726186831923270015874178287
Other News of Note;
Wave goodbye to passwords: Soon you could unlock your PC just by holding up your hand
Hitachi Europe has developed Biometric technology that could allow PC users to unlock their computer via their webcam by scanning veins in their fingers.
Password management is a critical component of IT maintenance. Many users do not take password security seriously, using easily guessed weak passwords to protect critical information. Biometrics are already being used on modern smartphones and Microsoft's Hello technology that allows you to login with your face.
Entire article at;
https://www.zdnet.com/article/wave-goodbye-to-passwords-the-veins-in-your-fingers-could-soon-unlock-your-pc/?ftag=TRE0fb9d06&bhid=2219791
Apple unveils new iPhone 11 and iPhone 11 Pro
Apple has introduced 2 new iPhones as well as a new iPad. The base starter phone, iPhone 11 is even priced $50 less than it's predecessor. However,
"Apple kept the starting prices of its more advanced models, the iPhone 11 Pro and iPhone 11 Pro Max, at $1,000 and $1,100. The company unveiled the new phones at a 90-minute press event at its Silicon Valley campus."
Apple has rebranded its iPhone line to make the iPhone 11 its entry-level option while adding a “Pro” label to its more expensive models.
https://www.nytimes.com/2019/09/10/technology/iphone-11.html
https://www.cnbc.com/2019/09/10/apple-hardware-event-new-iphones-apple-watches-and-more.html?__source=facebook%7Cmain&fbclid=IwAR21xsWe9ebXPC9DSnCSmyDnEFj8cxRI74ooaKmW82JdvWzJVI64H7NNOOQ
George Soros offers rare praise for Trump and how he’s handled Huawei in the trade war
https://www.cnbc.com/2019/09/10/soros-offers-rare-praise-for-trumps-handling-of-huawei-in-trade-war.html
Wednesday, August 21, 2019
Windows 10 Report Card after 4 years. Fake News: Mr. Science Bill Nye - Chromebook better than Windows
Windows 10 after four years: A solid report card, but serious challenges ahead
Every year, some pundits declare the PC dead. But sales are holding steady and are even up year over year, as mobile professionals, gamers, and corporate IT departments decide that there really isn't a credible alternative yet. Maybe next year.
After 4 years, 6 major feature updates Windows 10 is on track to hold 80% of the Windows market by the time support for Windows 7 ends in 2020. However, a number of corporate users refusal to upgrade sparks concerns that a resurgence of malware such as the WannaCry ransomware outbreak that struck Windows XP when support ended for that OS.
All in all Windows 10 has been a successful venture other than the misstep that occurred with the rollout of version 1809, (score under Upgrades and Updates).
ZDNet grades Windows 10 in 6 areas;
1. Adoption Rate: C-
2. Upgrades and Updates: C+
3. Privacy: A, The competition (Google and Apple) has made this category too easy for Microsoft.
4. Security: A/B
5. Apps: Incomplete
6. Hardware: A- Apple is stumbling badly in the Mac market, criticized for the quality of its keyboards, a lackadaisical approach to design, and a lackadaisical attitude about its professional customers. This year, the run of bad news for would-be Mac owners continues with the news that recent-vintage 15-inch MacBook Pro models are banned from airplanes because of the risk of battery fires.
To read the entire ZDNet article click the following link;
https://www.zdnet.com/article/windows-10-report-card-after-four-years-serious-challenges-ahead/
The above article segues nicely into our next news item, Mr. Science Bill Nye becoming the face of Chromebook. Is it time to take Mr. Nye's well paid for opinion and buy a Chromebook over a Windows notebook? After the Chromebook ad featuring Mr. Nye appeared, a ZDNet reporter decides to pay a visit to a retailer and find out which is selling and which is the best system to own.
Windows or Chromebook? A Best Buy salesman told me it isn't even close
After Google hires Bill Nye to explain that people are just scared to leave their decrepit Windows laptops for Chromebooks, I thought I'd get another opinion. It was harsh.
To read the surprise finding of the visit, please click on the following link;
https://www.zdnet.com/article/windows-or-chromebook-a-best-buy-salesman-told-me-it-isnt-even-close/?ftag=TRE-03-10aaa6b&bhid=2219791
Every year, some pundits declare the PC dead. But sales are holding steady and are even up year over year, as mobile professionals, gamers, and corporate IT departments decide that there really isn't a credible alternative yet. Maybe next year.
After 4 years, 6 major feature updates Windows 10 is on track to hold 80% of the Windows market by the time support for Windows 7 ends in 2020. However, a number of corporate users refusal to upgrade sparks concerns that a resurgence of malware such as the WannaCry ransomware outbreak that struck Windows XP when support ended for that OS.
All in all Windows 10 has been a successful venture other than the misstep that occurred with the rollout of version 1809, (score under Upgrades and Updates).
ZDNet grades Windows 10 in 6 areas;
1. Adoption Rate: C-
2. Upgrades and Updates: C+
3. Privacy: A, The competition (Google and Apple) has made this category too easy for Microsoft.
4. Security: A/B
5. Apps: Incomplete
6. Hardware: A- Apple is stumbling badly in the Mac market, criticized for the quality of its keyboards, a lackadaisical approach to design, and a lackadaisical attitude about its professional customers. This year, the run of bad news for would-be Mac owners continues with the news that recent-vintage 15-inch MacBook Pro models are banned from airplanes because of the risk of battery fires.
To read the entire ZDNet article click the following link;
https://www.zdnet.com/article/windows-10-report-card-after-four-years-serious-challenges-ahead/
The above article segues nicely into our next news item, Mr. Science Bill Nye becoming the face of Chromebook. Is it time to take Mr. Nye's well paid for opinion and buy a Chromebook over a Windows notebook? After the Chromebook ad featuring Mr. Nye appeared, a ZDNet reporter decides to pay a visit to a retailer and find out which is selling and which is the best system to own.
Windows or Chromebook? A Best Buy salesman told me it isn't even close
After Google hires Bill Nye to explain that people are just scared to leave their decrepit Windows laptops for Chromebooks, I thought I'd get another opinion. It was harsh.
To read the surprise finding of the visit, please click on the following link;
https://www.zdnet.com/article/windows-or-chromebook-a-best-buy-salesman-told-me-it-isnt-even-close/?ftag=TRE-03-10aaa6b&bhid=2219791
Thursday, August 1, 2019
Free Dark Web Check - see if your email and information is compromised on the Dark Web
Dark Web Check, Deep Web, Clearnet. Deep Dark secrets of the Internet.
There is a place on the Internet that is the domain of criminals, hackers, and others that are inaccessible to most users. They are only accessible via the use of special browsers or access to P2P (peer to peer networks) maintained for use only by members.
There is a place on the Internet that is the domain of criminals, hackers, and others that are inaccessible to most users. They are only accessible via the use of special browsers or access to P2P (peer to peer networks) maintained for use only by members.
In this deep forbidden layer, SSNs, credit card, bank info, personal info, email addresses and of course passwords are for sale along with other items. Drugs, vile pornography maybe even human trafficking occurs in this realm, transactions often protected by indecipherable Bitcoin accounts and links to hide identities.
Wikipedia: The Dark Web, The dark web is the World Wide Web content that exists on darknets, overlay networks that use the Internet but require specific software, configurations, or authorization to access. The dark web forms a small part of the deep web, the part of the Web not indexed by web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web.
The darknets which constitute the dark web include small, friend-to-friend peer-to-peer networks, as well as large, popular networks like Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnet due to its unencrypted nature.[8] The Tor dark web may be referred to as onionland,[9] a reference to the network's top-level domain suffix .onion and the traffic anonymization technique of onion routing.
With the latest Information breach at Capital One affecting over 100 million Americans, it is a good idea to check to see if your information is available on the Dark Web. There is a website that I have written about here before, "Have I Been Pawned" where you can enter your email address and it will report back how many breaches and what breaches your information has been compromised through.
When I first wrote about the Have I Been Pawned website in November of 2018, https://dforceatl.blogspot.com/2018/11/email-and-identity-theft-has-your.html
there were over 5.5 billion compromised accounts. Since that post the number has grown to 8.2 billion pawned accounts.
I have 4 main email accounts that I use, 1 for non-business related email, 1 I use to communicate with my clients and 2 Outlook accounts I use when in the field. In November my non-business account I found on the Dark Web but my business-related account was not listed. Today, the original account found on the Dark Web is on there but now my main business-related account is listed 3 times with recent hacks. One of my Outlook accounts is on the Dark Web, associated with the River City Media Spam list so my only risk there is an increase in spam.
The "Have I Been Pawned" site is safe to use and it is the same website that is used by Experian, Equifax, and other credit monitoring agencies. By going directly to the website, you don't have to provide a credit card or create an account with the Credit agency to check your info.
I cannot stress enough practicing good Password Policy!
That link again to "Have I Been Pawned" is https://haveibeenpwned.com/
Support for Windows 7 is ending
January 14, 2020 is the end of support by Microsoft for Windows 7. If you are still using Windows 7,
this means that your Intel processor and operating system are old and more vulnerable to security risks and viruses.
If you continue to use Windows 7 after support has ended, your PC will still work, but it may become more vulnerable to security risks and viruses. Your PC will continue to start and run, but Microsoft will no longer provide the following support for your business.
https://www.microsoft.com/en-us/microsoft-365/windows/end-of-windows-7-support
New DForce Intel Gen 8 & 9 processors with Windows 10 and Solid State Drives.
When I first wrote about the Have I Been Pawned website in November of 2018, https://dforceatl.blogspot.com/2018/11/email-and-identity-theft-has-your.html
there were over 5.5 billion compromised accounts. Since that post the number has grown to 8.2 billion pawned accounts.
I have 4 main email accounts that I use, 1 for non-business related email, 1 I use to communicate with my clients and 2 Outlook accounts I use when in the field. In November my non-business account I found on the Dark Web but my business-related account was not listed. Today, the original account found on the Dark Web is on there but now my main business-related account is listed 3 times with recent hacks. One of my Outlook accounts is on the Dark Web, associated with the River City Media Spam list so my only risk there is an increase in spam.
The "Have I Been Pawned" site is safe to use and it is the same website that is used by Experian, Equifax, and other credit monitoring agencies. By going directly to the website, you don't have to provide a credit card or create an account with the Credit agency to check your info.
I cannot stress enough practicing good Password Policy!
That link again to "Have I Been Pawned" is https://haveibeenpwned.com/
Support for Windows 7 is ending
January 14, 2020 is the end of support by Microsoft for Windows 7. If you are still using Windows 7,
this means that your Intel processor and operating system are old and more vulnerable to security risks and viruses.
If you continue to use Windows 7 after support has ended, your PC will still work, but it may become more vulnerable to security risks and viruses. Your PC will continue to start and run, but Microsoft will no longer provide the following support for your business.
https://www.microsoft.com/en-us/microsoft-365/windows/end-of-windows-7-support
New DForce Intel Gen 8 & 9 processors with Windows 10 and Solid State Drives.
Monday, July 29, 2019
Louisiana governor declares state emergency after local ransomware outbreak
The Governor of Louisiana has declared a statewide emergency after 3 school districts have been hit by ransomware. The attack has taken down IT networks and their files have been encrypted rendering them inaccessible.
Last year the Governor of Colorada activated a state emergency after the Colorado DOT was shut down due to SamSam ransomware.
Read the entire article at:
https://www.zdnet.com/article/louisiana-governor-declares-state-emergency-after-local-ransomware-outbreak/
IRS warns thousands of cryptocurrency holders to pay their taxes
Did you make a bundle on Bitcoin or some other Cryptocurrency last year? Uncle Sam wants his cut so get ready to pay up.
https://www.msn.com/en-us/money/markets/irs-warns-thousands-of-cryptocurrency-holders-to-pay-their-taxes/ar-AAEUqU2
Apple News
Apple 15-inch MacBook Pro (2019) review: 8-core power and portability, at a price
https://www.zdnet.com/product/apple-macbook-pro-15-inch-2019/?ftag=TRE0fb9d06&bhid=2219791
At $249, this iPad may be a great deal (or about to be discontinued)
Apple slashes the price of iPad as people are balking at paying high prices. Apple's new MacBook Air is significantly slower than the older model it replaces.
https://www.zdnet.com/article/at-249-this-ipad-may-be-a-great-deal-or-about-to-be-discontinued/
DForce Intel Gen 8 & 9 based workstations with SSDs
The Governor of Louisiana has declared a statewide emergency after 3 school districts have been hit by ransomware. The attack has taken down IT networks and their files have been encrypted rendering them inaccessible.
Last year the Governor of Colorada activated a state emergency after the Colorado DOT was shut down due to SamSam ransomware.
Read the entire article at:
https://www.zdnet.com/article/louisiana-governor-declares-state-emergency-after-local-ransomware-outbreak/
IRS warns thousands of cryptocurrency holders to pay their taxes
Did you make a bundle on Bitcoin or some other Cryptocurrency last year? Uncle Sam wants his cut so get ready to pay up.
https://www.msn.com/en-us/money/markets/irs-warns-thousands-of-cryptocurrency-holders-to-pay-their-taxes/ar-AAEUqU2
Apple News
Apple 15-inch MacBook Pro (2019) review: 8-core power and portability, at a price
https://www.zdnet.com/product/apple-macbook-pro-15-inch-2019/?ftag=TRE0fb9d06&bhid=2219791
At $249, this iPad may be a great deal (or about to be discontinued)
Apple slashes the price of iPad as people are balking at paying high prices. Apple's new MacBook Air is significantly slower than the older model it replaces.
https://www.zdnet.com/article/at-249-this-ipad-may-be-a-great-deal-or-about-to-be-discontinued/
DForce Intel Gen 8 & 9 based workstations with SSDs
Tuesday, July 9, 2019
Microsoft warns about Astaroth malware campaign, Hackers steal $3 million from Bank in Bangladesh.
Microsoft warns about Astaroth malware campaign
New hard-to-detect Astaroth campaigns spotted using fileless execution and living-off-the-land techniques.
Malware writers have found a new way to circumvent your anti-virus software. They are using a technique called "living off the land." This involves using legitimate tools to download code and process the illegal activity completely in the memory of the computer without using files.
The Microsoft Team behind Windows Defender ATP spotted the attacks. A member of the team said they were alerted when a huge and sudden spike in usage of the WMIC tool, "Windows Management Instrumentation Command-Line" tool. WMIC is a powerful tool that complements the existing management and administration utilities and tools. It is a command line shell much like the CMD command.
The sudden spike was indicative of a pattern that occurs during malware campaigns.
When Microsoft looked closer, it discovered a malware campaign that consisted of a massive spam operation that was sending out emails with a link to a website hosting a .LNK shortcut file.
If users were careless to download and run this file, it would launch the WMIC tool, and then a plethora of other legitimate Windows tools, one after the other.
The tools would all download additional code and pass their output to one another, executing solely in memory -- in what's called fileless execution -- and without saving any files on disk, making the job of classic antivirus solutions harder, as they would have nothing to file on disk to scan.
What is a .LNK file, these are files that point to the location of an executable file typically located on a hard drive. Your desktop shortcuts are examples of this. However in the case of the malware email, the .LNK file points to a URL on the internet where the malicious file is stored.
The end result of this attack is that the Astaroth trojan is downloaded and run. It is a known info-stealer that can dump credentials for a wide category of apps and uploaded the stolen data to a remote server.
This trojan first appeared in 2018. Earlier this year it was used in malware attacks targeting European and Brazilian users in February, this year.
The next step in the evolution of modern antivirus products is shifting from a classic file signature detection mode of operation to a behavioral-driven approach, where they can also detect "invisible" actions like fileless (in-memory) execution and living-off-the-land techniques where legitimate tools are abused for bad operations.
Be very careful opening emails from people you do not know, especially those containing links to external sites.
To read the full story click on this link;
https://www.zdnet.com/article/microsoft-warns-about-astaroth-malware-campaign/?ftag=TREc64629f&bhid=2219791
In other hacking and malware news;
Sodinokibi ransomware is now using a former Windows zero-day
The Sodinokibi malware uses a former Windows Zero-day vulnerability to carry out its attack on infected hosts.
The vulnerability, a privilege escalation flaw known as CVE-2018-8453, had been patched in the October 2018 Patch Tuesday Microsoft security updates after it had previously been used by a state-sponsored hacking group known as FruityArmor since August 2018.
I know updates can be a pain but with so many ransomware attacks occurring today, it is imperative that you patch/update your systems so they remain safe from attack.
https://www.zdnet.com/article/sodinokibi-ransomware-is-now-using-a-former-windows-zero-day/
'Silence' hackers hit banks in Bangladesh, India, Sri Lanka, and Kyrgyzstan, allegedly stole $3 million from Bangladesh's Dutch Bangla Bank.
In a report shared with ZDNet prior to publication, Group-IB tied the Dutch Bangla Bank incident to a group of hackers known as "Silence."
The group, which ZDNet previously covered in a September 2018 piece, has been active since 2016 and has historically targeted banks in Russia, former Soviet states, and Eastern Europe.
https://www.zdnet.com/article/silence-hackers-hit-banks-in-bangladesh-india-sri-lanka-and-kyrgyzstan/
DFORCE - Intel 8th & 9th Generation computers with Solid State Drives
New hard-to-detect Astaroth campaigns spotted using fileless execution and living-off-the-land techniques.
Malware writers have found a new way to circumvent your anti-virus software. They are using a technique called "living off the land." This involves using legitimate tools to download code and process the illegal activity completely in the memory of the computer without using files.
The Microsoft Team behind Windows Defender ATP spotted the attacks. A member of the team said they were alerted when a huge and sudden spike in usage of the WMIC tool, "Windows Management Instrumentation Command-Line" tool. WMIC is a powerful tool that complements the existing management and administration utilities and tools. It is a command line shell much like the CMD command.
The sudden spike was indicative of a pattern that occurs during malware campaigns.
If users were careless to download and run this file, it would launch the WMIC tool, and then a plethora of other legitimate Windows tools, one after the other.
The tools would all download additional code and pass their output to one another, executing solely in memory -- in what's called fileless execution -- and without saving any files on disk, making the job of classic antivirus solutions harder, as they would have nothing to file on disk to scan.
What is a .LNK file, these are files that point to the location of an executable file typically located on a hard drive. Your desktop shortcuts are examples of this. However in the case of the malware email, the .LNK file points to a URL on the internet where the malicious file is stored.
The end result of this attack is that the Astaroth trojan is downloaded and run. It is a known info-stealer that can dump credentials for a wide category of apps and uploaded the stolen data to a remote server.
This trojan first appeared in 2018. Earlier this year it was used in malware attacks targeting European and Brazilian users in February, this year.
The next step in the evolution of modern antivirus products is shifting from a classic file signature detection mode of operation to a behavioral-driven approach, where they can also detect "invisible" actions like fileless (in-memory) execution and living-off-the-land techniques where legitimate tools are abused for bad operations.
Be very careful opening emails from people you do not know, especially those containing links to external sites.
To read the full story click on this link;
https://www.zdnet.com/article/microsoft-warns-about-astaroth-malware-campaign/?ftag=TREc64629f&bhid=2219791
In other hacking and malware news;
Sodinokibi ransomware is now using a former Windows zero-day
The Sodinokibi malware uses a former Windows Zero-day vulnerability to carry out its attack on infected hosts.
The vulnerability, a privilege escalation flaw known as CVE-2018-8453, had been patched in the October 2018 Patch Tuesday Microsoft security updates after it had previously been used by a state-sponsored hacking group known as FruityArmor since August 2018.
I know updates can be a pain but with so many ransomware attacks occurring today, it is imperative that you patch/update your systems so they remain safe from attack.
https://www.zdnet.com/article/sodinokibi-ransomware-is-now-using-a-former-windows-zero-day/
'Silence' hackers hit banks in Bangladesh, India, Sri Lanka, and Kyrgyzstan, allegedly stole $3 million from Bangladesh's Dutch Bangla Bank.
In a report shared with ZDNet prior to publication, Group-IB tied the Dutch Bangla Bank incident to a group of hackers known as "Silence."
The group, which ZDNet previously covered in a September 2018 piece, has been active since 2016 and has historically targeted banks in Russia, former Soviet states, and Eastern Europe.
https://www.zdnet.com/article/silence-hackers-hit-banks-in-bangladesh-india-sri-lanka-and-kyrgyzstan/
DFORCE - Intel 8th & 9th Generation computers with Solid State Drives
Tuesday, June 11, 2019
How Hackers profit from your stolen medical data. US to demand 5 years of social media, email info for Visa application
How Hackers profit from your stolen medical data.
Data breaches have become so commonplace that people don't take notice of them as they should. Everyone is aware of illegal activities associated with stolen credit cards numbers that are used to make forgeries and illegal purchases, stolen ID and SSNs used in identity theft, but of greater value to cyber criminals are information stolen from health care facilities and institutions.
Stolen info based on health care records include not only personal/financial information but insurance documents, stolen doctor licenses, medical diplomas and more
"A hacker compromises the corporate network of a healthcare provider to find administrative paperwork that would support a forged doctor's identity. The hacker then sells to a buyer or intermediary (who then sells to the buyer) for a high enough price to ensure a return on investment but low enough to ensure multiple people buy the item.
The buyer poses as the stolen doctor's identity and submits claims to Medicare or other medical insurance providers for high-end surgeries."
The costs are high and only getting worse. HIPAA was enacted in 1996. Google, Inc. was founded in 1998. It could be time to revamp HIPAA and the way our medical information is protected.
Please read more at; https://www.zdnet.com/article/this-is-how-hackers-make-money-from-your-stolen-medical-data/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
US to demand five years of your social media, email account info in visa application
The US State Department will now require new visitors to the United States to hand over their social media account names as well as email addresses and phone numbers used over the past five years.
The data demand will apply to tourists and potential immigrants.
https://www.zdnet.com/article/us-visa-agency-will-now-demand-your-social-media-email-account-info/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
Intel Workstations - Solid State Drive based, Gen 8 & 9 Ultra Fast!
Data breaches have become so commonplace that people don't take notice of them as they should. Everyone is aware of illegal activities associated with stolen credit cards numbers that are used to make forgeries and illegal purchases, stolen ID and SSNs used in identity theft, but of greater value to cyber criminals are information stolen from health care facilities and institutions.
Stolen info based on health care records include not only personal/financial information but insurance documents, stolen doctor licenses, medical diplomas and more
"A hacker compromises the corporate network of a healthcare provider to find administrative paperwork that would support a forged doctor's identity. The hacker then sells to a buyer or intermediary (who then sells to the buyer) for a high enough price to ensure a return on investment but low enough to ensure multiple people buy the item.
The buyer poses as the stolen doctor's identity and submits claims to Medicare or other medical insurance providers for high-end surgeries."
The costs are high and only getting worse. HIPAA was enacted in 1996. Google, Inc. was founded in 1998. It could be time to revamp HIPAA and the way our medical information is protected.
Please read more at; https://www.zdnet.com/article/this-is-how-hackers-make-money-from-your-stolen-medical-data/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
US to demand five years of your social media, email account info in visa application
The US State Department will now require new visitors to the United States to hand over their social media account names as well as email addresses and phone numbers used over the past five years.
The data demand will apply to tourists and potential immigrants.
https://www.zdnet.com/article/us-visa-agency-will-now-demand-your-social-media-email-account-info/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
Intel Workstations - Solid State Drive based, Gen 8 & 9 Ultra Fast!
Tuesday, May 21, 2019
Microsoft kicks off the rollout of the Windows 10 May Update/1903
Microsoft's Windows 10 May Update/1903 is available to consumers and business customers as of today, May 21. It's available through WSUS, Windows Update for Business and VLSC starting today, too.
Starting today May 21, 2019, consumers and businesses can upgrade to the version 1903, the first feature update to Windows 10 in 2019. The update is available via download on WSUS, Windows Update for Business.
The latest version available prior to 1903 was version 1809. You can check which version you are on by using the Windows key + R, the type "Winver" and press the key. If you are not on version 1809, you can download and install version 1903 without doing the intermediary updates since Windows updates are cumulative.
Users can still delay by 35 days the update however Microsoft is not pushing it on users currently. Microsoft indicated in April that it was changing the way it rolls out updates to users after the troubles caused by the October 2018/1809 update that caused data loss for some users.
The new update has many new features including "SandBox" which allows Windows Pro, Enterprise and Education users to run potential risky software isolated helping to keep your system safe and secure.
https://www.zdnet.com/pictures/windows-10-update-the-new-features-that-matter-most/16/
I will be updating my system tonight and let you know how it goes.
For the entire story click on the link below;
https://www.zdnet.com/article/microsoft-kicks-off-the-rollout-of-the-windows-10-may-update-1903/?ftag=TREc64629f&bhid=2219791
Starting today May 21, 2019, consumers and businesses can upgrade to the version 1903, the first feature update to Windows 10 in 2019. The update is available via download on WSUS, Windows Update for Business.
The latest version available prior to 1903 was version 1809. You can check which version you are on by using the Windows key + R, the type "Winver" and press the
Users can still delay by 35 days the update however Microsoft is not pushing it on users currently. Microsoft indicated in April that it was changing the way it rolls out updates to users after the troubles caused by the October 2018/1809 update that caused data loss for some users.
The new update has many new features including "SandBox" which allows Windows Pro, Enterprise and Education users to run potential risky software isolated helping to keep your system safe and secure.
https://www.zdnet.com/pictures/windows-10-update-the-new-features-that-matter-most/16/
I will be updating my system tonight and let you know how it goes.
For the entire story click on the link below;
https://www.zdnet.com/article/microsoft-kicks-off-the-rollout-of-the-windows-10-may-update-1903/?ftag=TREc64629f&bhid=2219791
Wednesday, May 15, 2019
Warning! If You Save your Passwords in a Browser, Don't miss this Blog Post
If you use your favorite internet browsing program to save passwords for websites, you might want to rethink this policy. This includes all browser programs, Chrome, Firefox, IE and Safari. In 3 of these, I found the saved passwords were only protected by a user's password or in the case of Safari, the Admin password. The other major browser has a default policy of no password and will expose passwords with a few clicks of the mouse, however, it does allow you to set a Master password separate from a user password.
If you continue to use this method to save passwords please use a strong password and not one you use for all your protection including websites. However, if your browser uses a User or Admin password to protect saved website passwords, I have programs that can crack a forgotten password or generate a new password for a user. In the event your computer is stolen or accessed by a hacker or criminal, they can simply change your password and then proceed to steal your financial website's user name and password.
Lastly, beware this information is readily available using a Googe search.
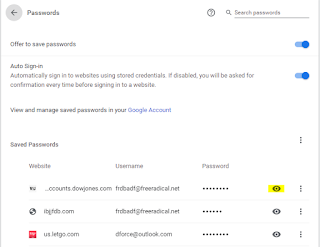
Google Chrome
By default, passwords in Chrome's password list are masked by dots to prevent one from seeing the actual password, however by simply clicking on the eye icon next to a password Windows will prompt you for your user login password or pin and voila, all passwords can be viewed by clicking on the eye icon to the right of a saved password.
If you have ever shared your password with a family member, co-worker or haphazardly use easy passwords for protection then any financial, confidential or social media sites you visit that have a saved password can be viewed and compromised. And let me add this, if I know this then hackers and criminals know this and if your computer is compromised by a trojan or malware then they know where to look to get access to your confidential Financial and Personal information. These steps are easily found by Googling for the information.
To illustrate how to expose your password info under Chrome, click on the 3 dots in a line, upper right corner of Chrome browser, then select Settings from the drop-down.
Next click on Passwords,
When you do this the saved and not saved Password list appears
Once the list appears, all I have to do is click on the eye icon and the system will respond with the following Window asking for the computer password/pin.
Once you have provided the computer with the correct password/pin, Chrome will then allow you to reveal the hidden password for every saved account.
Below is my IBJJF password exposed (since changed)...
You might think all this is bad enough but no, there's more.
I have a Chromebook and Android phones. If you have provided your Gmail account to these devices and have Sync and personalize Chrome across your devices turned on, you can go to My Google and find all saved passwords from your Chrome and Android based devices.
Mozilla Firefox and Microsoft Internet Explorer
You may think I'm saying not to use Google Chrome or I am picking on Chrome. I started with Chrome because it is the most popular Windows Browser now. However, FireFox and IE both have the same issue.
The default setting for Firefox doesn't require you to provide a password/pin to show passwords. All you have to do in Firefox is click on the settings icon in the upper right of the Firefox browser, select options,
choose Privacy & Security,
next click on Login & Passwords, Saved Logins.
click on Saved Logins and you are 1 step away for revealing all saved passwords.
Note: Mozilla does allow you to "Use a master password" which you will want to do. This is a better option in my opinion than using the user password for a computer, however as stated this is not the default and Mozilla is wide open otherwise.
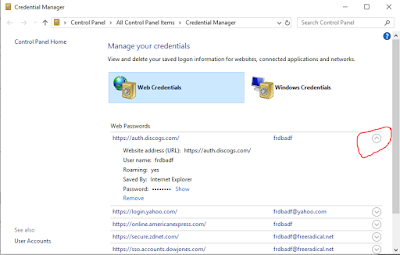
Internet Explorer
To accomplish the same feat in IE, go to Internet Tools. If your browser has the Menu Bar option on simply click on Tools and then select Internet Tools from the dropdown, if you don't see the Menu Bar you can access Internet Tools from the Control Panel.
Next click on the Content Tab and select Settings under AutoComplete
Click on Manage Passwords
To expose a password click on the carat symbol to the right of the password.
As you can see the user ID is already there, you will be asked to provide the user password/pin to reveal the password.
Safari
Apple's Safari browser protects Macs behind the Admin password. This is only as secure as the password is strong and breakable using 3rd party hacker software.
Tuesday, May 7, 2019
Ransomware, Malware attacks - Protection is important but a Recovery Plan is equally important, Israel responds to Hamas hackers with Air Strike
Ransomware: The key lesson Maersk learned from battling the NotPetya attack
In 2017 Maersk the shipping giant based in Denmark was hit by the NotPetya Ransomware. Maersk was not an intended target by the developers. NotPetya was developed by the Russian military and assisted by a leaked version of the NSA EternalBlue Hacking tool which helped to spread the WannaCry ransomware outbreak. NotPetya's intended target was businesses located in Ukraine, however, it was soon out of control and spreading and causing damage around the world costing billions of dollars in lost revenue and IT costs.
Ransomware and malware require constant vigilance and protection to prevent it from affecting your organization. With many nation states and their intelligence agencies focussed on cyberwarfare against one another, it is a daunting task. It was a worm developed by the NSA "Stuxnet" that brought down the Iranian centrifuges in their nuclear laboratories in 2010. Stuxnet like NotPetya was not contained and soon in the hands of criminal hackers wreaking havoc in businesses around the world.
But while protecting networks and critical systems is the ultimate goal, a data recovery plan must also be in place, so in the event of the worst happening and critical services being knocked out, you can still operate.
A significant part of this, said Woodcock, is "that ability to really understand the core business processes" and know everything about the systems and applications which run the operation.
I personally use redundant backup devices and software at my business clients. It is imperative that there is also backups kept offline in the event of the malware spreading to the backup devices.
To read more about what happened at Maersk;
https://www.zdnet.com/article/ransomware-the-key-lesson-maersk-learned-from-battling-the-notpetya-attack/
Windows Update: why it is important to update your systems and computers.
As new security holes are discovered and exploited, Microsoft releases updates patching these security risks. Computers that have not been patched or are using an old operating system are targeted by criminal hackers.
NSA's arsenal of Windows hacking tools has leaked
The NSA and other intelligence agencies are also targeting computers around the world. The NSA used Windows hacking tools to target several banks.
A new trove of alleged surveillance tools and exploits from the National Security Agency's elite hacking team have been released by the Shadow Brokers' hacking group.
The group Friday appeared to release tools designed to target Windows PCs and servers, along with presentations and files purporting to detail the agency's methods of carrying out clandestine surveillance.
https://www.zdnet.com/article/shadow-brokers-latest-file-drop-shows-nsa-targeted-windows-pcs-banks/
In a first, Israel responds to Hamas hackers with an air strike
Three years ago, NATO proclaimed "cyber" as a target in the modern era creating a new battlefield. Israel has now been the first to use military force to strike against a foe for using cyber warfare. Hamas had been engaging in attacks on Israel's cyberspace. In response, Israel launched an airstrike against as building in the Gaza strip housing Hamas cyber operatives.
"After dealing with the cyber dimension, the Air Force dealt with it in the physical dimension," said IDF spokesperson, Brig. Gen. Ronen Manlis. "At this point in time, Hamas has no cyber operational capabilities."
You don't want to miss this; read more at;
https://www.zdnet.com/article/in-a-first-israel-responds-to-hamas-hackers-with-an-air-strike/
If you are still running Windows XP and Windows 7, look to upgrade today to a new computer.
New DForce Intel 8th and 9th Generations Workstations.
In 2017 Maersk the shipping giant based in Denmark was hit by the NotPetya Ransomware. Maersk was not an intended target by the developers. NotPetya was developed by the Russian military and assisted by a leaked version of the NSA EternalBlue Hacking tool which helped to spread the WannaCry ransomware outbreak. NotPetya's intended target was businesses located in Ukraine, however, it was soon out of control and spreading and causing damage around the world costing billions of dollars in lost revenue and IT costs.
Ransomware and malware require constant vigilance and protection to prevent it from affecting your organization. With many nation states and their intelligence agencies focussed on cyberwarfare against one another, it is a daunting task. It was a worm developed by the NSA "Stuxnet" that brought down the Iranian centrifuges in their nuclear laboratories in 2010. Stuxnet like NotPetya was not contained and soon in the hands of criminal hackers wreaking havoc in businesses around the world.
But while protecting networks and critical systems is the ultimate goal, a data recovery plan must also be in place, so in the event of the worst happening and critical services being knocked out, you can still operate.
A significant part of this, said Woodcock, is "that ability to really understand the core business processes" and know everything about the systems and applications which run the operation.
I personally use redundant backup devices and software at my business clients. It is imperative that there is also backups kept offline in the event of the malware spreading to the backup devices.
To read more about what happened at Maersk;
https://www.zdnet.com/article/ransomware-the-key-lesson-maersk-learned-from-battling-the-notpetya-attack/
Windows Update: why it is important to update your systems and computers.
As new security holes are discovered and exploited, Microsoft releases updates patching these security risks. Computers that have not been patched or are using an old operating system are targeted by criminal hackers.
NSA's arsenal of Windows hacking tools has leaked
The NSA and other intelligence agencies are also targeting computers around the world. The NSA used Windows hacking tools to target several banks.
A new trove of alleged surveillance tools and exploits from the National Security Agency's elite hacking team have been released by the Shadow Brokers' hacking group.
The group Friday appeared to release tools designed to target Windows PCs and servers, along with presentations and files purporting to detail the agency's methods of carrying out clandestine surveillance.
https://www.zdnet.com/article/shadow-brokers-latest-file-drop-shows-nsa-targeted-windows-pcs-banks/
In a first, Israel responds to Hamas hackers with an air strike
Three years ago, NATO proclaimed "cyber" as a target in the modern era creating a new battlefield. Israel has now been the first to use military force to strike against a foe for using cyber warfare. Hamas had been engaging in attacks on Israel's cyberspace. In response, Israel launched an airstrike against as building in the Gaza strip housing Hamas cyber operatives.
"After dealing with the cyber dimension, the Air Force dealt with it in the physical dimension," said IDF spokesperson, Brig. Gen. Ronen Manlis. "At this point in time, Hamas has no cyber operational capabilities."
You don't want to miss this; read more at;
https://www.zdnet.com/article/in-a-first-israel-responds-to-hamas-hackers-with-an-air-strike/
If you are still running Windows XP and Windows 7, look to upgrade today to a new computer.
New DForce Intel 8th and 9th Generations Workstations.
Monday, April 29, 2019
Implantable Medical Devices - keeping them safe from Hackers, also Facebook will be taken over by the Dead in 50 years!
The future of cybersecurity: Your body as a hacker-proof network
Could a 'body area network' be the key to keeping medical devices safe or transferring data between individuals?
Modern medicine is making use of the internet with more devices having internet connectivity. Insulin pumps, pacemakers, and more implantable devices are being fitted with wireless internet connectivity that allows doctors to monitor your health remotely.
The issue with being connected to the internet is that the devices can be hacked. Already proof of concept attacks has illustrated the risk exists. Fortunately, there have been no attacks so far but cybercriminals have demonstrated a lack of morality and tampering with these devices will no doubt happen. In the past, they have extorted hospitals putting patients at risk.
The wireless technology used to share data can be read many feet away. Recently implantable defibrillators were given a severity rating of 9.3 out of 10 for a flaw that allowed them to be hacked 20 feet away by the Department of Homeland security.
Scary stuff but new research using the human body as the signal carrier restricts the signal to a few centimeters outside the patient. Researchers at Purdue University have created Electro-Quasistatic Human Body Communication (EQS-HBC) which uses low-frequency, carrier-less broadband transmission.
To read the full article click on the link below.
https://www.zdnet.com/article/the-future-of-cyber-security-your-body-as-a-hacker-proof-network/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
The dead will take over Facebook in the next 50 years
Analysis suggests that the deceased will soon outnumber the living on the network.
and I thought it was me the reason no one responded to my posts. :-)
A time is coming in which you may see more memorial accounts on Facebook than active users, with academics estimating that accounts belonging to the deceased will outnumber the living within 50 years.
https://www.zdnet.com/article/the-dead-will-take-over-facebook-in-the-next-50-years/?ftag=TRE-03-10aaa6b&bhid=2219791
Could a 'body area network' be the key to keeping medical devices safe or transferring data between individuals?
Modern medicine is making use of the internet with more devices having internet connectivity. Insulin pumps, pacemakers, and more implantable devices are being fitted with wireless internet connectivity that allows doctors to monitor your health remotely.
The issue with being connected to the internet is that the devices can be hacked. Already proof of concept attacks has illustrated the risk exists. Fortunately, there have been no attacks so far but cybercriminals have demonstrated a lack of morality and tampering with these devices will no doubt happen. In the past, they have extorted hospitals putting patients at risk.
The wireless technology used to share data can be read many feet away. Recently implantable defibrillators were given a severity rating of 9.3 out of 10 for a flaw that allowed them to be hacked 20 feet away by the Department of Homeland security.
Scary stuff but new research using the human body as the signal carrier restricts the signal to a few centimeters outside the patient. Researchers at Purdue University have created Electro-Quasistatic Human Body Communication (EQS-HBC) which uses low-frequency, carrier-less broadband transmission.
To read the full article click on the link below.
https://www.zdnet.com/article/the-future-of-cyber-security-your-body-as-a-hacker-proof-network/?ftag=TRE49e8aa0&bhid=27630927001468733386426006914379
The dead will take over Facebook in the next 50 years
Analysis suggests that the deceased will soon outnumber the living on the network.
and I thought it was me the reason no one responded to my posts. :-)
A time is coming in which you may see more memorial accounts on Facebook than active users, with academics estimating that accounts belonging to the deceased will outnumber the living within 50 years.
https://www.zdnet.com/article/the-dead-will-take-over-facebook-in-the-next-50-years/?ftag=TRE-03-10aaa6b&bhid=2219791
Subscribe to:
Comments (Atom)
-
I encourage my clients to forward questionable emails to me for analysis to check if they are valid or not. Recently a forwarded email came...
-
Microsoft's Patch Tuesday to end beginning with Windows 10. This change goes for both security updates and non-security updates. htt...
-
Acer C7 Chromebook from Google Play, $199 What can you get for $199? Dual-core Intel Celeron Processor 2 GB DDR3 RAM 320 GB hard d...